Agenda
- What is DHCP and how DHCP works?
- What is DHCP relay Agent and how it works?
- What is DHCP snooping?
- Why do we need DHCP snooping?
- How DHCP snooping works?
There are two ways of assigning an IP address on a device:
- Static
- Automatic:we use protocol so that the device can obtain its IP address automatically (dynamically).
DHCP (Dynamic Host Configuration Protocol) is used to provide automatic “IP address” and other info such as subnet mask, default gateway, IP address lease time, and domain name server (DNS) to device which is configured to get IP address automatically.
DHCP runs over the UDP means it’s a connectionless Protocol. DHCP uses Port 67 when connecting to server and 68 when connecting to Client.
Process of IP Assignment by DHCP:
Let’s say Eva-wr01 is acting as DHCP server and R2 is acting as DHCP Client.

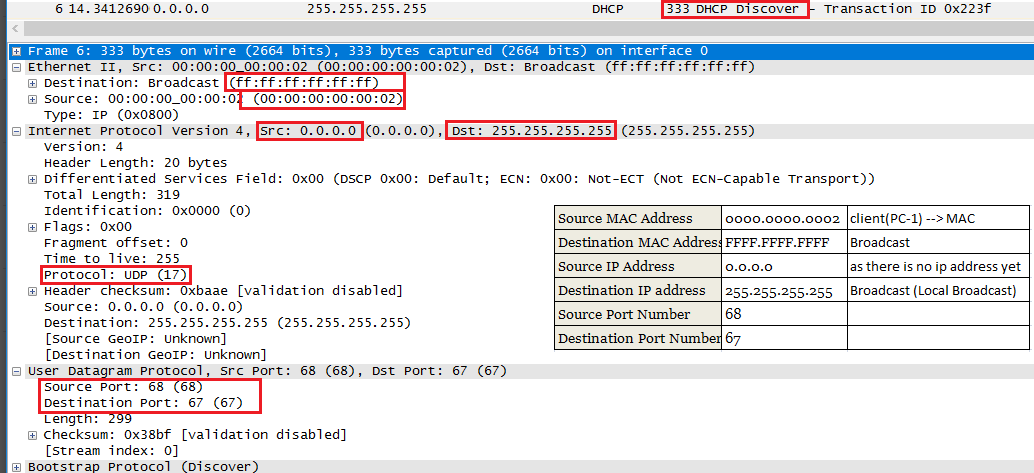
1. When a device which is configured to use DHCP Server to get IP address starts, Device sends a DISCOVER message as broadcast using below info.
Here we have to notice that Source MAC address is own MAC address (0000.000.0002) of R2 and source IP address is 0.0.0.0 as there is no ip address.
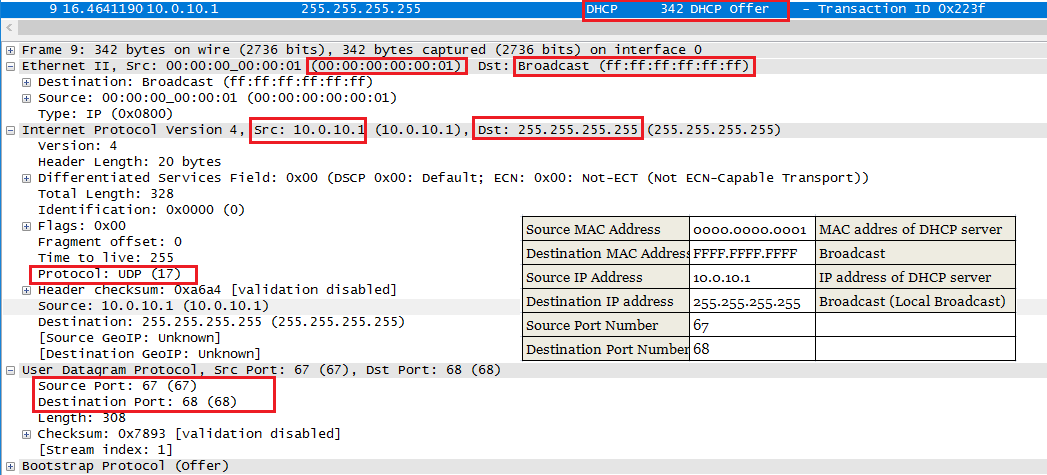
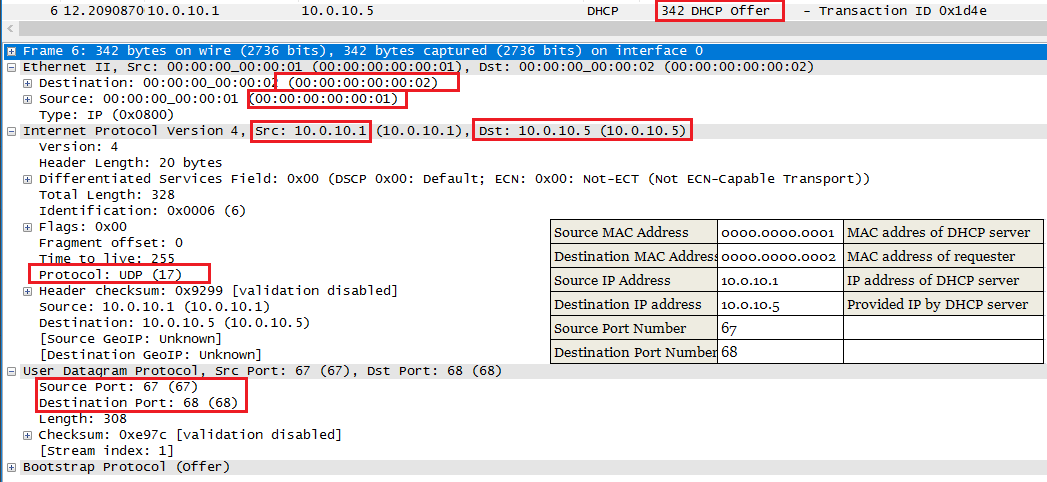
2. When DHCP server received this request, then sends an OFFER packet (Broadcast or Unicast depending on broadcast flag is 1 or 0) back to client using below info.
When the DHCP client sends a discover requesting an IP address. The DHCP server listens to this broadcast flag and broadcasts the reply packet if the flag is set to 1.If the “no ip dhcp-client broadcast-flag” command is entered, the broadcast flag is set to 0 and the DHCP server unicasts the reply packets to the client with the offered IP address.
DHCPOFFER message contain information such as subnet mask, default gateway, IP address of DHCP server, lease time, and domain name server (DNS).
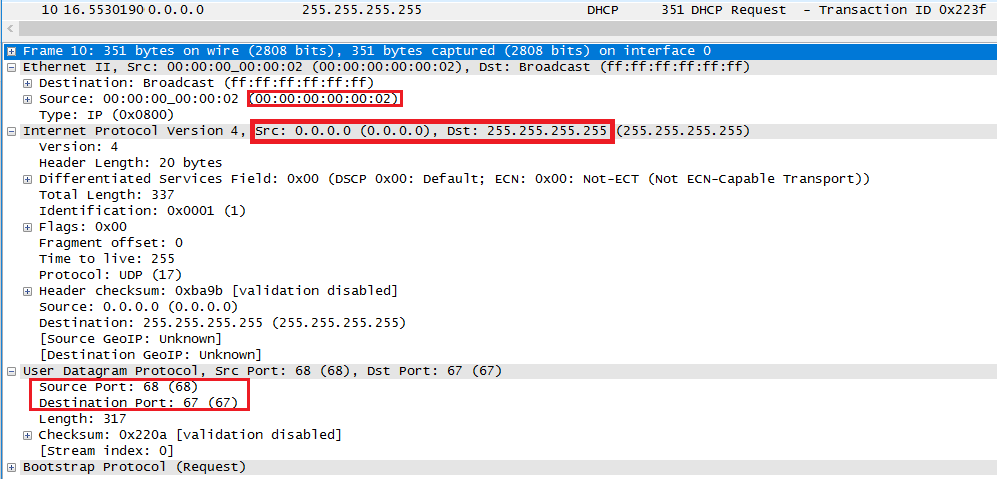
3. When Client receives a DHCP offer, it respond with DCHP request as broadcast.
The client broadcasts a DHCPREQUEST message that MUST include the ‘server
identifier’ option to indicate which server it has selected, and that MAY include other options specifying desired configuration values. The ‘requested IP address’ option MUST be set to the value of ‘yiaddr’ in the DHCPOFFER message from the server.
4. DHCP Server assigned the IP to client computer and sends a ACK packet as Broadcast or Unicast depending on broadcast flag is 1 or 0 to client.

DHCP Client State Machine:
1. Init: First state of client where client create a DHCP Discover message and broadcasts it. Client starts from this state if it’s configured to get IP automatically or lease ends, or lease negotiation fails.
2. Selecting: After sending DHCP Discover message client enters to Selecting state where it waits to receive DHCP offers from one or more DHCP servers.
3. Requesting: After receiving DHCP Offer message client goes to the requesting state and sends a DHCP Request message to the selected server. Client remains in the requesting state until it receives DHCP ACK from the server.
It checks provided IP is free to use or not if it’s free then records T1 and T2 timers according to the IP address lease time specified in the DHCP Ack message, and transits to the BOUND state.
While doing checks if client found like provided IP address is already is in use then it sends DHCPDELINE message back to server and starts again from INIT.
If client receive DHCPNAK from its selected server due to some reason then client returns to the INIT state.
4. Bound State: After Receiving DHCPACK message, client goes to the bound state and good to use provided IP address and other information.
When Client which already has vailed IP address but some reason someone rebooted it then it starts with INIT-Reboot.
5. INIT-REBOOT: In this state, a client PC broadcasts a DHCP Request message and then transits to the REBOOTING state. Here we have to notice that we are not starting with INIT state.
6. Rebooting:In the REBOOTING state, upon receiving a DHCP Ack message, a client PC sets T1 and T2 timers according to the IP address lease time specified in the DHCP Ack message, and then transits to the BOUND state.
7. Renewing: Client tries to renew the lease. To renew the lease client sends DHCP request message to server and if receives Reply then renew the lease and restarts the T1 and T2 Timers.If not receiving response from a server, it stays in standby, wait for a DHCPAck message, until T2 timer expired, and then transits to the REBINDING state.
IF client receives DHCPNAK from server then client moves to INIT state to get a new lease.
8. Rebinding: The client is failed to renew its lease with the server that originally granted it. In the REBINDING state, a client PC broadcasts a DHCP Request message on the subnet with no server specified so that all of DHCP servers can receive the message. In this state, if the client PC receives a DHCP Ack message from a DHCP server, it resets T1 and T2 timers and transits back to the BOUND state. IF client receives DHCPNAK then client goes into the INIT state or if client is not receiving reply prior to the expiration of the lease it goes back to the INIT state.
Some important filed in DHCP Packet:
Xid: –transaction ID, a random number chosen by the client, used by the client and server to associate messages and responses between a client and a server.
Ciaddr: –client IP address; only filled if client is in BOUND, RENEW or REBINDING state and can respond to ‘ARP’ requests.
Yiaddr: –‘your’ (client) IP address (set in DHCPOFFER and DHCPACK)
Giaddr: –Relay agent (gateway) IP address; filled in by the relay agent with the address of the interface through which Dynamic Host Configuration Protocol (DHCP) message was received.
Chaddr: – Client’s hardware address (Layer 2 address).
DHCP Relay Agent:
A DHCP relay agent is a device generally router that forwards DHCP packets between clients and servers. Relay agents are used to forward requests and replies between clients and servers when they are not on the same subnet.

Process:
1. As we know DHCP Client broadcasts a DHCP Discover message to find DHCP server. When the Router receives this message which is configured with DHCP Relay agent, it will forward the message to the DHCP Server as a Unicast Packet.
giaddr (Gateway IP address) is added in the DHCP Packet, this field will contains in our case the IP address 192.168.11.1 since the router receives the DHCP Discover message on the Fa0/0, and the source IP address of this Unicast packet will be 192.168.11.1.This field is required by the DHCP Server so it can know from which pool it has to select an IP address.
2. DHCP Server receives the DHCP Discover message, it will respond by the DHCP OFFER Message; this message will be sent as a Unicastpacket to the router. The router will forward the DHCP OFFER Message as a broadcast message.
3. The DHCP Client will verify the information in the DHCP Offer message, and sends a DHCP REQUEST as a broadcast message. The router will forward this message as Unicast packet to the DHCP SERVER.
4. The DHCP SERVER will send a DHCP ACK message to the router as unicast, and the router will broadcast this message on the Fa0/0.
DHCP Snooping
DHCP snooping is a security feature which is used to prevent DHCP spoofing.
DHCP spoofing is a man-in-the middle attack in that the attacker listens for DHCP Requests from clients and answers them with DHCP offer before the authorized DHCP offer comes to the clients. Let’s have a look in below topology:

Suppose that an attacker could bring up a rogue DHCP server on his machine in the same subnet as that same client PC. Now when the client broadcasts its DHCP request, the rogue server sends DHCP reply with its own IP address replacement as the default gateway. When the client receives the reply, it begins using the spoofed gateway address. Packets destined for addresses outside the local subnet then go to the attacker’s machine first. The attacker can forward the packets to the correct destination, but in the meantime, it can examine every packet that it intercepts.
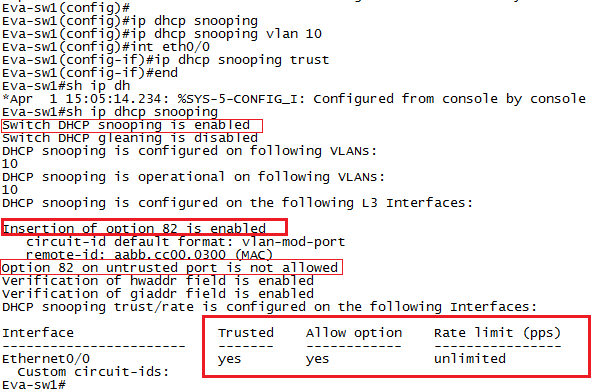
Configuration:
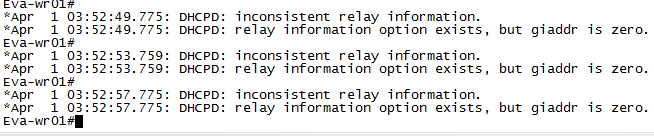
After configuring DHCP snooping using above commands, I found that PC1 is not getting IP Address so dig into it using debug for DHCP and came to know like Eva-wr01 is showing below logs.
Remember that by default, when we enable DHCP snooping on a Cisco switch it will insert option 82 information into DHCP packets moreover the switch will set the giaddr field of the DHCP packet to 0.0.0.0. As we already discussed about giadd in DHCP relay agent topic, we should know that by default Cisco routers acting as DHCP relays and DHCP servers will drop DHCP packets with the giaddr field set to 0.0.0.0.
we can configure ” no ip dhcp snooping information option” command so switch will not insert option 82 information into DHCP packet.




Like!! I blog frequently and I really thank you for your content. The article has truly peaked my interest.
Nice read, I just passed this onto a colleague who was doing a little research on that. And he just bought me lunch since I found it for him smile Therefore let me rephrase that: Thanks for lunch!